Write a Global Subscription Policy
Use Case
Compliance Requirement: Users can only interact with Dev data.
For this requirement, this organization should write a policy that allows users to only access Dev data. To do so, they will use the tags and attributes created in Chapter 2 to build their Global Subscription Policy to manage data access. The steps below use this scenario to illustrate the policy, but other policy builder options are noted throughout the tutorial.
Create a Global Subscription Policy
Best Practice: Write Global Policies
Build Global Subscription Policies using attributes and Discovered tags instead of writing Local Policies to manage data access. This practice prevents you from having to write or re-write single policies for every data source added to Immuta and from manually approving data access.
- Click the Policies icon in the left sidebar and select the Subscription Policies tab.
- Click Add Policy and complete the Enter Name field.
-
Select Allow users with specific groups/attributes from the first dropdown menu. Click the tabs below to view additional access restrictions and their instructions.
Allow Anyone
-
Check the Require users to take action to subscribe checkbox to turn off automatic subscription. Enabling this feature will require users to manually subscribe to the data source if they meet the policy.
-
Click the dropdown menu beneath Where should this policy be applied if you would like to allow any user to automatically get access to the data source when they request access.
Allow anyone who asks (and is approved)
-
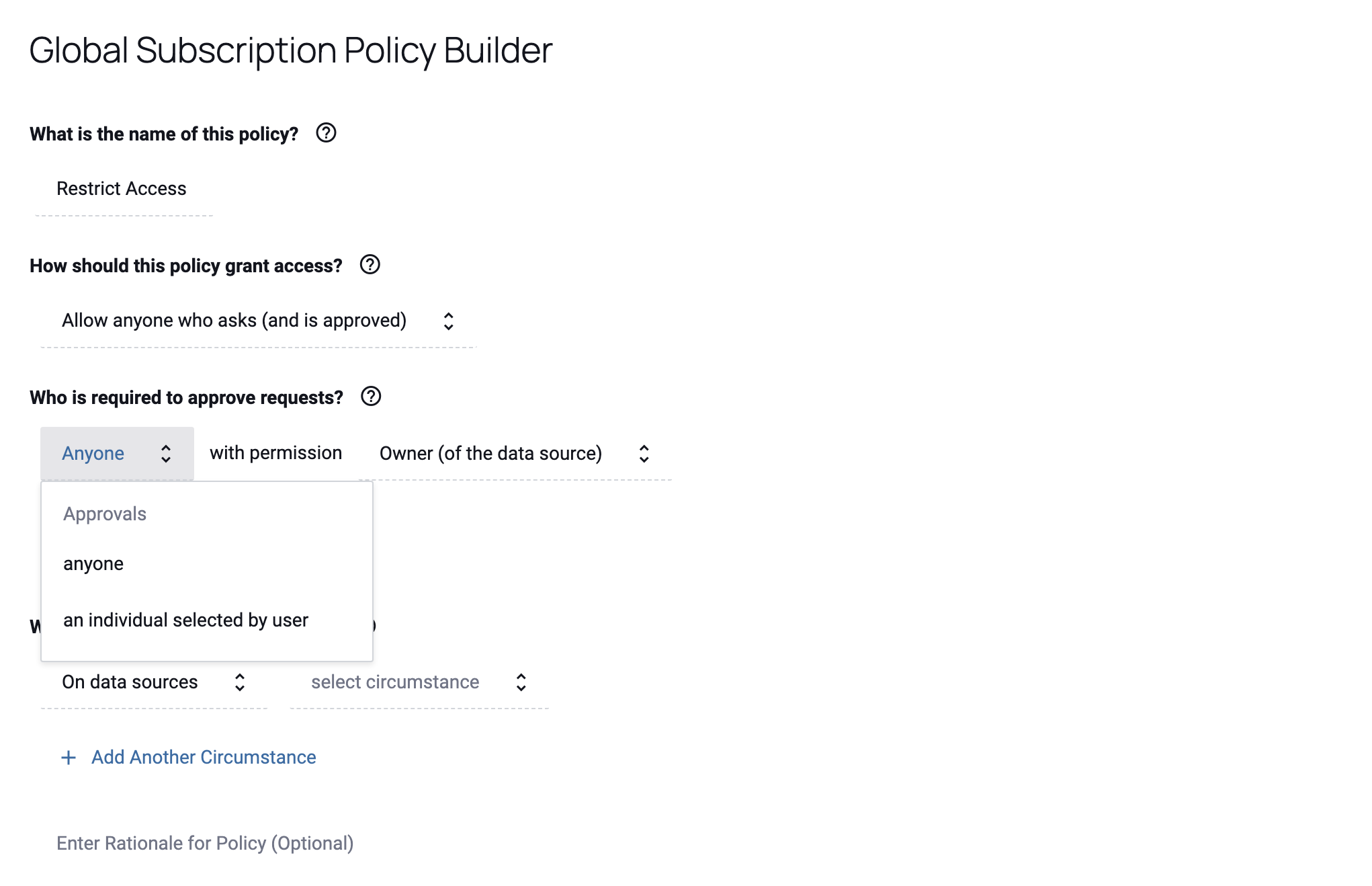
Click anyone or an individual selected by user from the first dropdown menu in the Subscription Policy Builder.
Note: If you choose an individual selected by user, when users request access to a data source they will be prompted to identify an approver with the permission specified in the policy and how they plan to use the data.
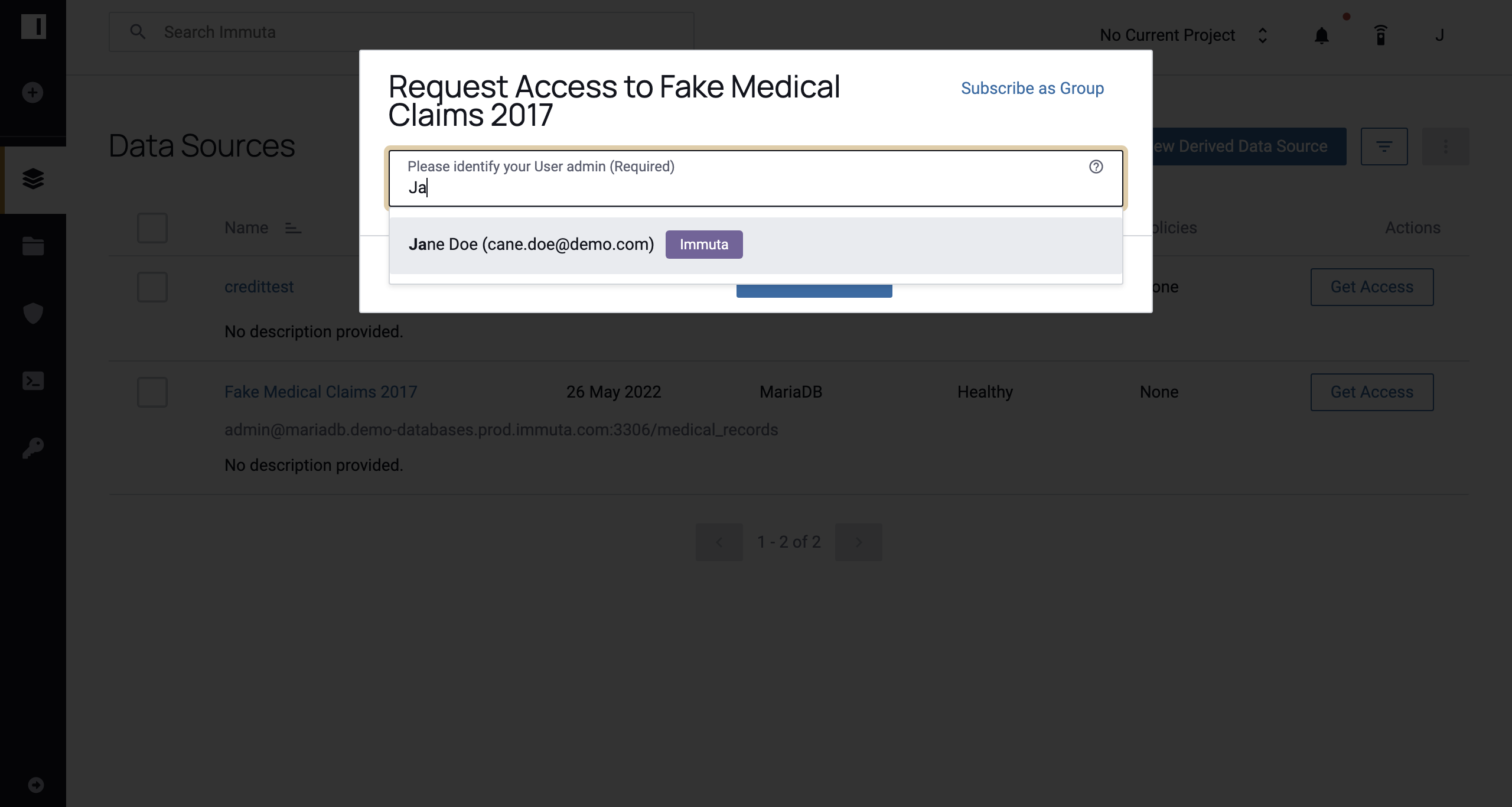
-
Select the Owner (of the data source), User_Admin, Governance, or Audit permission from the subsequent dropdown menu.
Note: You can add more than one approving party by selecting + Add and repeating steps a and b.
Individually Selected Users
Select this policy to grant access only to users who have been manually added to the data source.
-
-
Select possesses attribute,
Environment.devfrom the subsequent dropdown menus. You could also select is a member of group and choose a group as the condition to drive the policy.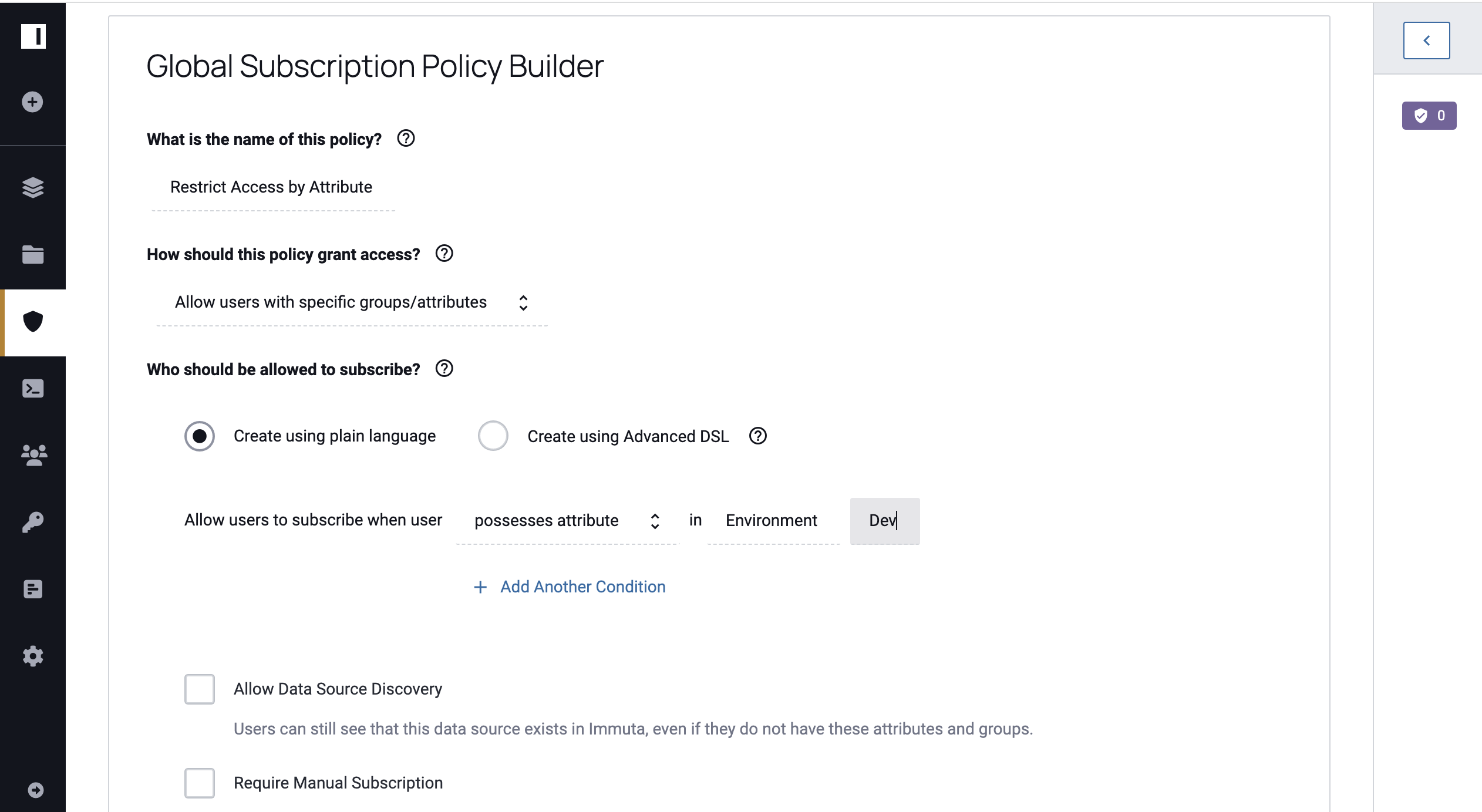
Alternatively, you can use the Advanced Rules DSL to create more complex policies than the Subscription Policy Builder allows by clicking Advanced Rules DSL in the top right corner of the policy builder. Complete the Enter Rules field with the available functions and variables: @database, @hasAttribute, @hasTagAsAttribute @hostname, @iam, @isInGroups, @schema, and @table. When you place your cursor in this field, a tooltip appears with the functions and values you can use to build your policy. For details about these functions and variables, see the Advanced DSL Policies overview.
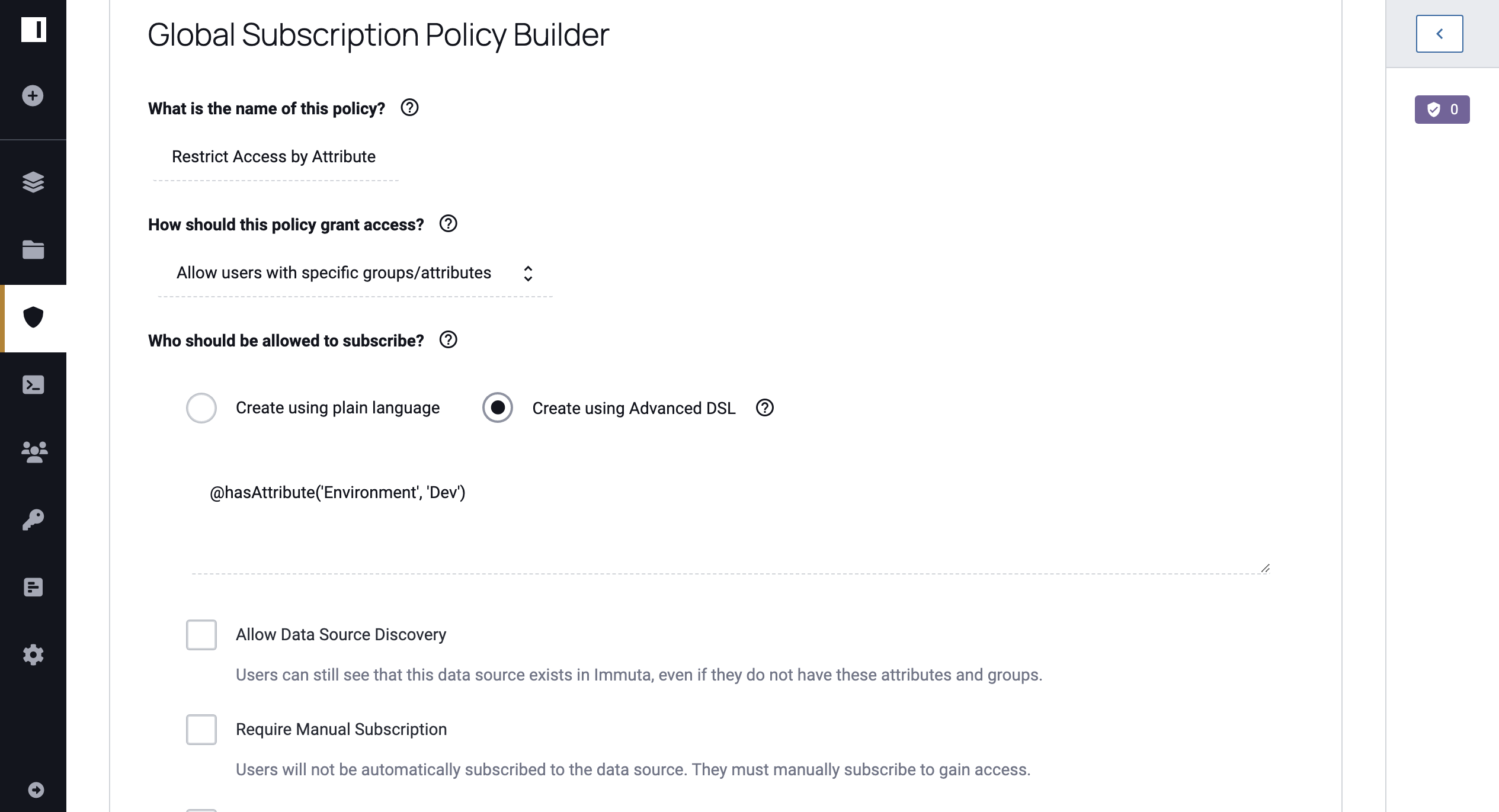
-
If you would like to make your data source visible in the list of all data sources in the UI to all users, click the Allow Data Source Discovery checkbox. Otherwise, this data source will not be discoverable by users who do not meet the criteria established in the policy.
Note: You can add more than one condition by selecting + ADD. The dropdown menu in the far right of the Subscription Policy Builder contains conjunctions for your policy. If you select or, only one of your conditions must apply to a user for them to see the data. If you select and, all of the conditions must apply.
-
Check the Require Manual Subscription checkbox to turn off automatic subscription. Enabling this feature will require users to manually subscribe to the data source if they meet the policy.
-
If you would like users to have the ability to request approval to the data source, even if they do not have the required attributes or traits, check the Request Approval to Access checkbox. This will require an approver with permissions to be set.
- Select anyone or an individual selected by the user from the first dropdown to specify who will be giving approvals.
- Select Owner, USER_ADMIN, GOVERNANCE, or AUDIT from the subsequent dropdown to specify the required permission(s) for giving approvals.
-
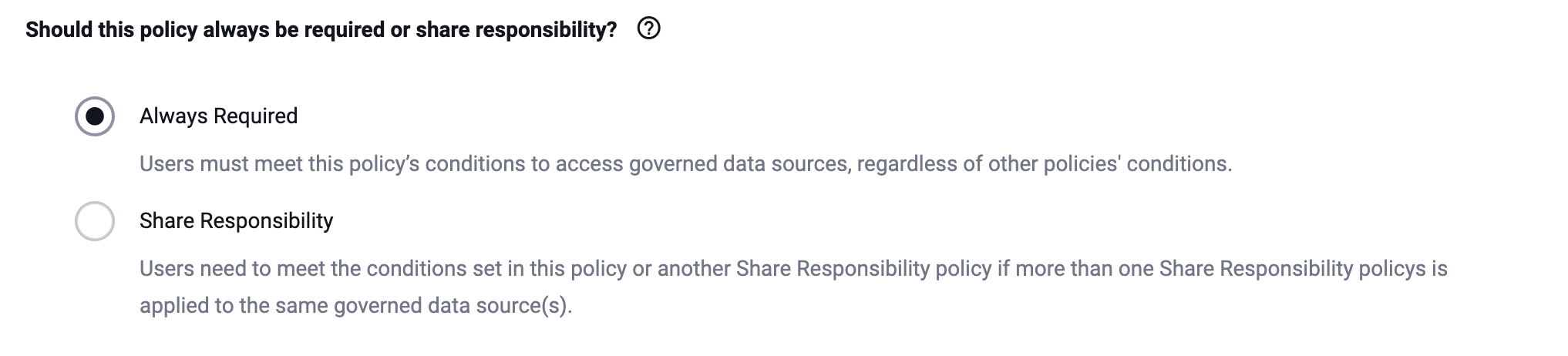
Select how you want Immuta to merge multiple Global Subscription policies that apply to a single data source.
-
Always Required: Users must meet all the conditions outlined in each policy to get access (i.e., the conditions of the policies are combined with
AND). -
Share Responsibility: Users need to meet the condition of at least one policy that applies (i.e., the conditions of the policies are combined with
OR).
Note: To make this option selected by default, see the App Settings page.
-
-
Select On data sources from the menu beneath Where should this policy be applied?. Additional options include When selected by data owners and On all data sources.
-
Select tagged and
Environment.Devfrom the subsequent menus. Additional options includewith columns tagged
Select this option and then search for tags in the subsequent dropdown menu.
with column names spelled like
Select this option, and then enter a regex and choose a modifier in the subsequent fields.
in server
Select this option and then choose a server from the subsequent dropdown menu to apply the policy to data sources that share this connection string.
created between
Select this option and then choose a start date and an end date in the subsequent dropdown menus.
-
Click Create Policy, and then click Activate Policy or Stage Policy.
Additional Subscription Policies
Most likely, you will have additional Subscription Policies to enforce. To do so, create separate Global Subscription Policies, and Immuta will use boolean logic to merge all the relevant policies on the tables they map to.
In the scenario discussed at the beginning of this tutorial, the compliance team would need to follow the same process
outlined here to write a Global Subscription Policy for Test data and a Global Subscription Policy for Prod data to
restrict access to accounts that have the attributes Environment.Test and Environment.Prod, respectively.